AFIO
Weekly Intelligence Notes #28-15 dated 14 July 2015
If you are having difficulties with the links or viewing this
newsletter when it arrives by email, members may view the
latest edition each week at this link: https://www.afio.com/pages/currentwin.htm You will need your LOGIN NAME and your PASSWORD.
[Editors' Note are now below the CONTENTS] REMOVAL INSTRUCTIONS: We do not wish to
add clutter to inboxes. To discontinue receiving the WINs, click here. |
CONTENTS
Section I - INTELLIGENCE HIGHLIGHTS
Section II -
CONTEXT & PRECEDENCE
Section
III - COMMENTARY
Section IV - Research Request
Section V - Upcoming Events
Upcoming AFIO Events
- 15 July 2015 - San Francisco, CA - The AFIO Andre LeGallo Chapter hosts John Lightfoot, Assistant Special Agent in Charge of the Counterterrorism branch in the FBI San Francisco Division.
- Saturday, 8 August 2015, 11am - 3pm - Orange Park, FL - AFIO North Florida Chapter Meeting with John Caulfield, "Intelligence and the Department of State."
- Tuesday, 11 August 2015 - MacDill AFB, Florida - The AFIO Suncoast Chapter hosts Karl D. Klicker, EdD, speaking on the Islamic State.
- 25-26 August 2015 - McLean, VA - Joint CIRA and AFIO 40th Anniversary Conference at CIA and a local hotel.
- Monday 28 September 2015 - New York, NY - AFIO Metro NY Chapter hears former FBI Special Agent Edward M. Stroz
- 16 November 2015, 12:30 pm - Los Angeles, CA - The AFIO - LA Chapter luncheon meeting with LA County Sheriff Jim McDonnell on Communications between Law Enforcement and Intelligence Agencies.
Other Upcoming Events
For Additional AFIO and other Events two+ months or more... Calendar of Events
WIN
CREDITS FOR THIS ISSUE: The WIN editors thank the
following special contributors: pjk, and fwr. They
have contributed one or more stories used in this issue.
The WIN editors
attempt
to include a wide range of articles and commentary in the
Weekly Notes
to inform and educate our readers. However, the views
expressed in the
articles are purely those of the authors, and in no way
reflect support
or endorsement from the WIN editors or the AFIO officers and
staff. We
welcome comments from the WIN readers on any and all articles
and
commentary. IMPORTANT: AFIO does not "vet" or endorse research
inquiries, career announcements, or job offers. Reasonable-sounding
inquiries and career offerings are published as a service to our
members, and for researchers, educators, and subscribers. You are urged
to exercise your usual caution and good judgment when responding, and
should verify the source independently before supplying any resume,
career data, or personal information.]
If you are having difficulties with the links or viewing this
newsletter when it arrives by email, members may view the
latest edition each week at this link: https://www.afio.com/pages/currentwin.htm You will need your LOGIN NAME and your PASSWORD.
MORE...STEPTOE's CYBERLAW PODCASTS
Steptoe Cyberlaw Podcast Resources for Cybersecurity, Privacy & National Security:
AFIO's Board Member Stewart Baker, with Steptoe & Johnson, joins law colleagues, industry leaders, and others for weekly interviews released as informative Cyberlaw Podcasts.
The interviews are on late-breaking topics with major national
security, legal, and cyber experts. Here are a few of the latest links to the mp3 files:
Steptoe Cyberlaw Podcast – Topics: Unbreakable Encryption; Hackers Hacked; the Right to be Forgotten - 15 July 2015
Discussants:
Stewart A. Baker, Alan Cohn, Meredith Rathbone, Michael Vatis, Jason M. Weinstein on federal law enforcements’ issues with unbreakable encryption; Hacking Team was itself hacked; and the right to be forgotten still on the offensive. In our second half we have an interview with Michael Casey, former senior columnist for the Wall Street Journal and – as of last week – senior advisor at the MIT Media Lab’s Digital Currency Initiative, the author, along with his former Wall Street Journal colleague Paul Vigna, of The Age of Cryptocurrency: How Bitcoin and Digital Money Are Challenging the Global Economic Order. The views expressed in this podcast are those of the speakers and do not reflect the opinions of the firm.
Interview with Catherine Lotrionte, Assoc Dir
Institute for Law, Science, Global Security at Georgetown University, on
7 July 2015
Discussants: Stewart A. Baker, Michael Vatis, Jason M.
Weinstein China�s new security law; FTC settles with a virtual currency
mining app makers; This Week in Hacks: FBI report ties Anthem and OPM
hack; Anthem class action filed; OPM class action; FTC releases new
security guidance; Foreign Intelligence Surveillance Court reauthorizes
metadata program; WikiLeaks rolls out more alleged NSA docs; Russia
modifies its right to be forgotten bill. In our second half we have an
interview with Catherine Lotrionte, Associate Director of the Institute
for Law, Science and Global Security at Georgetown University.
Interview with Robert Knake, Sr Fellow for Cyber Policy at the CFR on 30 June 2015
Discusses: attribution and the Astros Hack; WikiLeaks says NSA
spied on French leaders; Google fights for Jake Applebaum; cyberattacks
on Polish flight network; Google joins the fight on online harassment;
and Toshiba and quantum cryptography. In the second half they have an
interview with Robert Knake, Senior Fellow for Cyber Policy at the
Council on Foreign Relations, where we discuss the OPM hack,
attribution, and the pros and cons of norms.
Interview with James Baker, General Counsel, FBI on 23 June 2015
Discussants: Stewart A. Baker, Michael Vatis, Jason M.
Weinstein, Alan Cohn cover growing threats to free speech: France�s
censorship of Google; the European Court of Human Rights endorses
liability for intermediaries; the Right to be Forgotten returns to
Russia; Houston Astros� database hack; FBI faces criticism over stingray
disclosures and aerial surveillance; US Supreme Court boosts privacy
rights in hotel case; White House orders all .gov sites to use SSL
encryption; FISA court decides it doesn�t need an amicus; Sony is still
at risk in an employee class action for the data breach; Hackback gets
interest from a Congressional hearing; and In Other News: Jacob
Applebaum appeals to the Chinese to release OPM files to Wikileaks;
Glenn Greenwald stands up for Russia. In our second half we have an
interview with James Baker, General Counsel of the FBI, where we discuss
the FBI�s aerial surveillance capabilities, stingrays, �Going Dark,�
encryption, and the bureau�s attribution of cyberattacks. The views
expressed in this podcast are those of the speakers and do not reflect
the opinions of the firm.
Subscribe to the Cyberlaw Podcast here. Now also on iTunes and Pocket Casts!
Also suggested is to explore Steptoe's superb Cyber Blog. And the main website for the list of prior Cyber Security podcasts is here.
|
|
|

There will be no Weekly Intelligence Notes next
Tuesday, 21 July 2015.
We will resume the following Tuesday, 28
July.
SPECIAL Announcements
EVENT RESTRICTIONS HAVE BEEN CHANGED: You can attend Day One at CIA
if you have been an employee, at some time, of any member agency of the Intelligence Community (or are now currently with,
or retired from, one of those agencies). A spouse
accompanying you may attend regardless of no prior IC employment. In a
few cases a nonspousal guest (check with us first) may attend as well.
Restrictions do not apply
to Day Two.

CIRA (Central Intelligence Retirees Association) and
AFIO (Association of Former Intelligence Officers) are
holding a joint conference and celebration of our 40th anniversaries
on 25-26 August 2015.
Day One - Tuesday, 25 August: This
celebration coincides with the next CIA Annuitant Reunion on 25 August
where many CIRA and AFIO members, who are CIA retirees, will be in
attendance.
AFIO and CIRA members who are CIA annuitants and who retired on an even year, have been invited directly by CIA and should sign up for
that day when the CIA invitation arrives in
your inbox. Annuitants of odd years who wish to attend may register
through the links below.
RESTRICTION: To attend Day One at CIA
you need to have been an employee, at some time, of any member agency of the Intelligence Community (or are now currently with,
or retired from, one of those agencies). A spouse accompanying you may
attend without prior IC employment. Restriction does not apply to Day
Two.
Day Two - Wednesday, 26 August: The
conference expands and continues on Day Two
at the Sheraton Tysons Hotel, with many CIA, CIRA, AFIO, and other IC
speakers and
panelists. This second day ends with a
"Spies in Black Ties"
Anniversary Reception and Awards Banquet.
 Invitation Letter to Members Invitation Letter to Members
 Tentative Agenda Tentative Agenda
To apply securely online, use form here.
To print-and-mail a  registration form, access it here. registration form, access it here.
If you have questions, contact afio@afio.com
Newly released Museum catalog from CIA:
Official OSS Exhibition Catalogue
 In the summer of 2011, the CIA Museum inaugurated a gallery dedicated to the Office of Strategic Services (OSS), the World War II outfit that was America’s first centralized intelligence agency. The Official OSS Exhibition Catalogue, like the gallery itself, brings the OSS legacy to life and suggests how the CIA reflects that legacy. Showcasing artifacts and photographs from the Museum collection, the catalogue covers the history of OSS from the Pearl Harbor attack through the dissolution of the OSS. Along the way, it introduces many trailblazers of US intelligence. In the summer of 2011, the CIA Museum inaugurated a gallery dedicated to the Office of Strategic Services (OSS), the World War II outfit that was America’s first centralized intelligence agency. The Official OSS Exhibition Catalogue, like the gallery itself, brings the OSS legacy to life and suggests how the CIA reflects that legacy. Showcasing artifacts and photographs from the Museum collection, the catalogue covers the history of OSS from the Pearl Harbor attack through the dissolution of the OSS. Along the way, it introduces many trailblazers of US intelligence.
Spotting Terrorists in America
Do any of your neighbors "look like" terrorists? If you are a SpyPedia subscriber - a database of the CiCentre - you would know what they might look like from these surprising statistics:
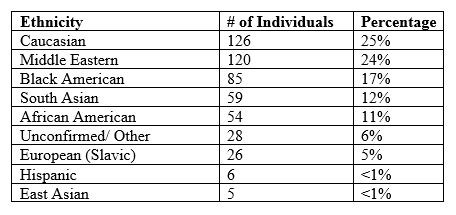
Be surprised every day...with the facts. Explore SpyPedia here.
AFIO Members...are you a victim of the OPM Data Breach?
 All notices regarding the breach will come
from CSID, a private identity protection company hired by OPM to provide
services to those affected by the data breach. The notice you receive
may be either an email or a mailed letter. If an email, it will come
from opmcio@csid.com; a letter will
be on CSID letterhead and will contain phone numbers and websites to
contact them. Every individual whose personal information has been
compromised will be covered by a $1 million identity theft protection
policy and will have access to full-service identity restoration
provided by CSID. In addition, you will be offered the option to enroll
in the CSID Protector Plus program - free of charge for 18 months. Other firms, e.g., Life Lock, offer similar programs. All notices regarding the breach will come
from CSID, a private identity protection company hired by OPM to provide
services to those affected by the data breach. The notice you receive
may be either an email or a mailed letter. If an email, it will come
from opmcio@csid.com; a letter will
be on CSID letterhead and will contain phone numbers and websites to
contact them. Every individual whose personal information has been
compromised will be covered by a $1 million identity theft protection
policy and will have access to full-service identity restoration
provided by CSID. In addition, you will be offered the option to enroll
in the CSID Protector Plus program - free of charge for 18 months. Other firms, e.g., Life Lock, offer similar programs.
Be CAUTIOUS. There are now many fake emails [phishing] being
sent to look like CSID or OPM. If you have received notification, you
should not click on any of the links and should, instead, visit the website established by CSID for OPM: www.csid.com/OPM. On this site you will be able to enroll in the program and get related information.
In addition to security guidelines sent to you separately by your agency and from CSID,
as well as placing fraud alerts on your credit accounts with
a credit reporting firm, here are a few additional suggestions for ID,
banking, and credit protection:
- The latest updates from OPM on this major breach of their data systems
- Watch video here by the National Counterintellience and Security Center (NCSC) Deputy Director.
- Slides from the program are here.
- FBI Guidance to Government Employees and Contractors is here and notes from an FBI SA presentation on ID Theft is here.
- The Office of the Inspector General, Social Security Administration provides the following guidelines.
- The US Department of Justice has issued these guidelines.
- Of interest is the Center for Identity Management and Information Protection at Utica College.
NEW Gift item....
 NEW: AFIO's Intelligence Community Mousepad NEW: AFIO's Intelligence Community Mousepad
Show your colors! The full colors of the seals of all 18 members of the US Intelligence
Community on this 8" round, slick surface, nonskid, rubber-backed mouse
pad. Price: $20.00 for 2 pads [includes shipping to US based address,
only. For foreign shipments, we will contact you with a
quote.] Great gift for colleagues and self. Click photo above for
larger image. Also we've heard some use it as a large drink coaster.
...ORDER NOW
|
Section
I - INTELLIGENCE HIGHLIGHTS
CIA, FBI Looking Into Forged Letter From Top Democrat on Ukraine. The request for comment reached Sen. Dick Durbin's staff just after midnight on Monday. What did the No. 2 Senate Democrat have to say about a letter, over his signature, in which he appeared to dictate to Ukrainian Prime Minister Arseniy Yatsenyuk who should be in his government? A Washington, DC-based reporter for Russian outlet RIA Novosti wanted to know.
The discovery of the letter appeared to be a huge propaganda coup for Moscow and pro-Russian separatists in Ukraine, who have argued that the government in Kiev is Washington's puppet.
"By the time the East Coast was awake, we had messages from State and our embassies flagging the issue for us as well," a Durbin aide told Yahoo News.
But the letter was a hoax. And not even a particularly well-executed one. Sure, Durbin's signature was capably duplicated, but everything else, from the stationery to Durbin's title, wasn't quite right. His leadership post in Congress isn't "assistant minority leader," it's "assistant Democratic leader." [Read more:
Knox/Yahoo/10July2015]
Senators Ask US Spy Chief to Inform Policymakers About Energy Boom. Four Republican senators on Tuesday urged the director of national intelligence to keep policymakers informed of the global security implications of booming US energy output as Congress considers repealing the ban on domestic oil exports.
"We agree that energy independence within North America and, perhaps, the Western Hemisphere is not only an attainable goal, but also increasingly the economic reality," Senators Lisa Murkowski, the head of the Senate energy committee, and Richard Burr, the head of the chamber's intelligence committee, and two others wrote in a letter to the Director of National Intelligence, James Clapper.
The senators said they support analysis by intelligence officials to "assess the geopolitical and international security implications of our nation's energy renaissance."
The letter cited a 2012 report from the National Intelligence Council - a bridge between the intelligence and policy communities - that suggested the United States could emerge as a major energy exporter by 2020. [Read more: Reuters/14July2015]
FBI Chief: Terrorist Group Turning to Encrypted Communications. The Islamic State terrorist group is increasingly using encrypted communications to recruit troubled Americans and urge them to carry out attacks, FBI Director James B. Comey told Congress on Wednesday.
Comey's testimony is the latest effort by the Obama administration to pressure Silicon Valley companies to design their products in ways that will allow law enforcement agencies to monitor communications that would otherwise be rendered unreadable by advances in encryption.
But the Obama administration also signaled for the first time that it may not seek legislation that would force technology companies to make changes that many think would undermine their security and commercial viability.
Deputy Attorney General Sally Yates, who also testified before the Senate Judiciary Committee, said the administration hoped that companies would comply voluntarily rather than have the government "cram down their throats" legislation requiring them to disable their own encryption systems. [Read more:
Nakashima/WashingtonPost/8July2015]
Argentina's New Intelligence Agency Targets Captains of Industry. On July 7, the Cristina Kirchner administration published a decree setting the new guidelines for Argentina's Federal Intelligence Agency (AFI) formed in January. The new intelligence agency will be tasked with unique roles, such as preventing "economic coups," bank runs, and currency offloads.
According to the addendum to decree 1311/2015, the agency will function as a "doctrinaire body aimed at laying the foundations for a process of profound reform and modernization of the National Intelligence System."
Following criticism that the former Secretariat of Intelligence was too prone to political manipulation, Kirchner has instructed the AFI not to "spy" on Argentinean citizens. Instead, the "national intelligence [system] should ensure the protection and care" of the public, she says.
The 408-page document also lays out how the government will handle future authorizations for wiretaps on intelligence targets, shifting responsibility from the judiciary to the Public Ministry. [Read more:
Marty/PanAmPost/10July2015]
Cyprus' Intelligence Chief Resigns After Spy Tech Revelations. The head of the island's secret service has resigned following revelations that it had been using phone surveillance technology, the government said on Saturday.
Andreas Pentaras' resignation was accepted by the president.
"Following the information and the shadows cast in relation to the use of specific software by KYP, and to protect the service's notable work to date, its chief... submitted his resignation today," a written statement from the government spokesman said.
Pentaras' resignation came after revelations a few days ago that KYP had apparently purchased phone surveillance tech from a manufacturer with a poor reputation among privacy advocates. [Read more:
Psyllides/CyprusMail/11July2015]
Waterford to Host Global Intelligence Forum. Intelligence officers, former US Secret Service agents, cybercrime experts and members of international police forces will convene in Co Waterford this week for the biennial Global Intelligence Forum.
Hosted by Mercyhurst University's Ridge School of Intelligence Studies, the forum will examine innovations in business intelligence, best practices for security analysis, global cybersecurity threats, the impact of social media in security and intelligence management, and the application of intelligence principles to higher education challenges.
Garda Commissioner N�ir�n O'Sullivan will address the event, along with former White House official for cybersecurity Howard Schmidt and former director of the US Secret Service Lewis Merletti.
Forum attendees will also hear from Europol's strategic analyst for the European Cybercrime Centre Jaroslav Jakubcek, Nama chairman Frank Daly, president-emeritus of Notre Dame College Andrew Roth, Liam Fahey of Babson College and Patrick Gibbons of UCD. [Read more:
Newenham/IrishTimes/13July2015]
Central Africa: Great Lakes Spy Chiefs in Kampala Over Terror Threat. Intelligence chiefs from the Great Lakes states will meet in Kampala, Uganda, tomorrow to discuss ways to counter the growing threats of terrorism in the region.
Kenya will be represented by NIS chief Maj Gen Philip Kameru.
Intelligence gathering and sharing is high on the agenda as al Shabaab continues to pose a threat.
The region, usually known as International Conference on the Great Lakes Region, are Kenya, Burundi, the Democratic Republic of Congo, Rwanda, Tanzania and Uganda. [Read more:
Mohamed/AllAfrica/13July2015]
Section II - CONTEXT
& PRECEDENCE
To Improve Security, Governments Need Accurate, Timely Intelligence. Effective security starts with accurate intelligence. Unfortunately, agencies short on budget and personnel may often lack timely access to information they can use to better protect their networks and users. Fortunately, there are several active players in the security community that aggregate and serve up intelligence through publicly available data feeds. Agencies can easily access some great resources for security intel that will go a long way toward helping secure their environments.
Speaking at the recent StateTech Cybersecurity Summit, Aamir Lakhani (also known as Dr. Chaos), a leading cybersecurity and cloud consultant and researcher, shared information on resources he recommends to government agencies looking for ways to improve their security situations.
Here are five resources that state and local governments can tap to improve their security strategies. [Read more:
Slagg/StateTech/10July2015]
What the CIA, Julia Child and Shark Repellent Have in Common. As "Shark
Week" draws to an end, the Central Intelligence Agency offered up a most unusual, yet fascinating history lesson to mark the occasion on its Twitter account.
While the operators of the spy agency's Twitter account have taken comedic, if sometimes perplexing, liberties with their social media activity in the past, none so far may top this GIF of TV cooking guru Julia Child clubbing a dead shark.
Even without context, the three-second clip is mesmerizing enough, but the CIA account then proceeded to outline how a young Julia Child once made her mark on US history outside of the culinary arts.
According to records from the US National Archives and Records Administration, Child joined the CIA's origin agency, the Office of Strategic Services, just after it was established during World War II in 1942. [Read more:
Mallin/ABCNews/10July2015]
Moxie Marlinspike: The Coder Who Encrypted Your Texts. In the past decade, Moxie Marlinspike has squatted on an abandoned island, toured the US by hopping trains, he says, and earned the enmity of government officials for writing software.
Mr. Marlinspike created an encryption program that scrambles messages until they reach the intended reader. It's so simple that Facebook Inc.'s WhatsApp made it a standard feature for many of the app's 800 million users.
The software is effective enough to alarm governments. Earlier this year, shortly after WhatsApp adopted it, British Prime Minister David Cameron called protected-messaging apps a "safe space" for terrorists. The following week, President Barack Obama called them "a problem."
That makes the lanky, dreadlocked and intensely private coder a central figure in an escalating debate about government and commercial surveillance. In a research paper released Tuesday, 15 prominent technologists cited three programs relying on Mr. Marlinspike's code as options for shielding communications. [Read more:
Yadron/WallStreetJournal/9July2015]
FBI Statement Before the Senate Select Committee on Intelligence. Good afternoon Chairman Burr, Vice Chairman Feinstein, and members of the committee. Thank you for the opportunity to appear before you today to discuss the widespread reach of terrorists' influence, which transcends geographic boundaries like never before. As technology advances so, too, does terrorists' use of technology to communicate - both to inspire and recruit. The widespread use of technology propagates the persistent terrorist message to attack US interests whether in the homeland or abroad. As the threat to harm Western interests evolves, we must adapt and confront the challenges, relying heavily on the strength of our federal, state, local, and international partnerships.
We continue to identify individuals who seek to join the ranks of foreign fighters traveling in support of the Islamic State of Iraq and the Levant, commonly known as ISIL, and also homegrown violent extremists who may aspire to attack the United States from within. These threats remain among the highest priorities for the FBI and the Intelligence Community as a whole.
Conflicts in Syria and Iraq continue to serve as the most attractive overseas theaters for Western-based extremists who want to engage in violence. We estimate upwards of 200 Americans have traveled or attempted to travel to Syria to participate in the conflict. While this number is lower in comparison to many of our international partners, we closely analyze and assess the influence groups like ISIL have on individuals located in the United States who are inspired to commit acts of violence. Whether or not the individuals are affiliated with a foreign terrorist organization and are willing to travel abroad to fight or are inspired by the call to arms to act in their communities, they potentially pose a significant threat to the safety of the United States and US persons.
ISIL has proven relentless in its violent campaign to rule and has aggressively promoted its hateful message, attracting like-minded extremists to include Westerners. To an even greater degree than al Qaeda or other foreign terrorist organizations, ISIL has persistently used the Internet to communicate. From a homeland perspective, it is ISIL's widespread reach through the Internet and social media which is most concerning as ISIL has aggressively employed this technology for its nefarious strategy. ISIL blends traditional media platforms, glossy photos, in-depth articles, and social media campaigns that can go viral in a matter of seconds. No matter the format, the message of radicalization spreads faster than we imagined just a few years ago. [Read more: FBI.gov/8July2015]
Final Intelligence Report From the Last Day of WW2 up for Auction. The final Allied intelligence report of World War Two stating that 'there is no longer an enemy to defeat' has emerged 70 years on along with an historic telex announcing the German surrender.
The intelligence summary came from the Cipher Office of the Allied forces which reported back to army top brass of any enemy movement in Europe after the Normandy invasion in June 1944.
In the last top secret message sent from the office on May 8, 1945 - VE Day - the document reads: 'For the first time in 11 months there is no contact with the enemy.'
'Today belongs to the men of this army who fought and conquered the enemy from Normandy to the Elbe.'
'There is no enemy situation to report for there is no longer an enemy to defeat.'
On the same day, Dwight D. Eisenhower, the supreme commander of the Allied forces, issued a series of telex messages confirming the signing of the surrender by the Germans and ordering an immediate cease fire. [Read more:
Tonkin/DailyMail/14July2015]
Unit 8200: Israel's Cyber Spy Agency. In a searingly hot afternoon at a campus-like new science park in Beer Sheva, southern Israel, I watched as a group of bright, geeky teenagers presented their graduation projects. Parents and uniformed army personnel milled around a windowless room packed with tables holding laptops, phones or other gadgets. There was excited chatter and a pungent smell of adolescent sweat.
This was a recent graduation ceremony for Magshimim (which roughly translates as "fulfilment"), the three-year after-school programme for 16 to 18-year-old students with exceptional computer coding and hacking skills. Magshimim serves as a feeder system for potential recruits to Unit 8200, the Israeli military's legendary high-tech spy agency, considered by intelligence analysts to be one of the most formidable of its kind in the world. Unit 8200, or shmone matayim as it's called in Hebrew, is the equivalent of America's National Security Agency and the largest single military unit in the Israel Defence Forces.
It is also an elite institution whose graduates, after leaving service, can parlay their cutting-edge snooping and hacking skills into jobs in Israel, Silicon Valley or Boston's high-tech corridor. The authors of Start-up Nation, the seminal 2009 book about Israel's start-up culture, described 8200 and the Israeli military's other elite units as "the nation's equivalent of Harvard, Princeton and Yale."
With a female IDF minder at my side, I listened as the teenagers described their projects. More than half were boys but there were girls too, and 8200 is open to both. Omer, 19, had designed a USB key that can suck information out of one computer and organise it on another: essentially, a hacking tool. "We made it appear like a keyboard so you can infiltrate any company in the world," he told me. "It's a proof of concept." [Read more:
Reed/FinancialTimes/10July2015]
Eric Roberts: The Spy Who Suffered. One of the UK's most brilliant wartime spies was poorly treated by colleagues at MI5 in the paranoid years of the Cold War and was left gripped by fear that he was suspected of being a traitor. Now an extraordinary letter and a series of family documents reveal the full story.
In the 1930s, Eric Roberts was a clerk with the Westminster Bank, where he seemed to be an average, unassuming employee.
But Roberts's real work was espionage. He had been a field agent for MI5 since the 1920s, recruited by famous spymaster Maxwell Knight, and infiltrating first communist then fascist groups.
In 1940, when Churchill became concerned about the activities of potential fifth columnists, Roberts was taken on as a full time agent by MI5. [Read more:
Berg/BBC/14July2015]
Section
III - COMMENTARY
Washington Can't Fix Computer Glitches. At a time when high-profile state-sponsored cyberattacks often grab headlines, tensions were high Wednesday after computer problems temporarily brought down the New York Stock Exchange and United Airlines.
The interruptions, according to the companies, were the result of internal computer glitches that happened to have worldwide consequences.
But Washington immediately turned to the security question. After the stock exchange went down, Sen. Bill Nelson told reporters that the incident had "all the appearances of a cyberattack." He later tweeted a call for Congress to act on cybersecurity legislation.
Members of Congress, presidential candidates, and President Obama have thrown their weight behind cybersecurity legislation that would facilitate cyberthreat-information sharing between the government and the private sector. [Read more:
Waddell/NationalJournal/8July2015]
The Intelligence Community Wins With DI2E
Plugfests. For more years than its members like to remember, the geospatial community has been trying to figure out a way to bring emerging capabilities to the US government customer base. Traditional cartography, imagery collection and imagery analysis is a tradecraft well known within the Intelligence Community (IC), but the common challenge of simply placing data over a map or image in a standardized fashion has yet to be solved.
The problems have been twofold: (1) there has been some doubt about the existence of a common path at all because standardization has eluded the IC and, for that matter, the entire whole of government; so (2) the geospatial community has in many cases given up, choosing to spend its research and development capital on commercial providers who are eager to find solutions that feed a new, fast-growing and profitable way of doing business.
Enter the Defense Intelligence Information Enterprise (DI2E), built on an understanding that the old way of doing business - federal dollars to spawn GEOINT ideas - is history, because those dollars are harder to come by. A reason for creating DI2E is finding solutions that can be used over and over again, often in different combinations with other technologoes - to facilitate standards that define layers of interoperability among Web services. In those solutions, the geospatial community is taking a step back into the future.
By participating in the annual DI2E Plugfest eXchanges, geospatial companies can leverage technology created for commercial customers, turning that technology into off-the-shelf, proven solutions to cope with working across a 17-member IC that has gone about its business in 17 different ways. Moreover, they can identify ground that has already been tread and look at complementing other technologies to result in a modular end product that is greater than the sum of its parts. [Read more:
Clark/DefenseSystems/14July2015]
The Future of US Intelligence: Adapting to Deal with China. In an April interview with Charlie Rose, former CIA Deputy Director Michael Morell told Charlie Rose that the US intelligence effort should focus on problems that only the Intelligence Community (IC) can do - and China was not one of them. Morell said "Anybody can give you an opinion of who's up and who's down in the Chinese Communist Party." The collapse of a China policy consensus, to paraphrase a recent commentator, however, demonstrates how wrong he is that anyone can evaluate China, its politics, and its future. It is quite possible the IC is the only place where China's veil of secrecy can be pierced and the perceptive analyst is free from retribution. But if accurately understanding Beijing and its intentions could have prevented US thinking on China from arriving at this tragic juncture, then intelligence policymakers need to reconsider the continuing importance of states and what it means to be an IC expert on China.
Assessing China remains one of the critical challenges for the US Intelligence Community, even as many would-be intelligence reformers condemn states to the dustbin of history and irrelevance for the future of US intelligence. As critical as I am of most writing on intelligence reform, the status quo for IC analysts and their careers, at least on China, cannot continue.
The United States needs the IC's effort on China, because of the severe limits placed upon public analysis. The vast amount of public information now available on China - sometimes including ostensibly internal-use periodicals - obscures how much important information remains out of reach to analysts reliant upon open sources and personal contacts. [Read more:
Mattis/NationalInterest/13July2015]
Research Request
Movie Project Seeks IC Officers Who Served in Bulgaria from 2001 Onwards. I am seeking officers of any nationality but especially US, Russia, Bulgarian, Romanian, and Turkish, who served in Bulgaria from 2001 onwards. This is in support of most interesting movie project that is funded and underway. For details and possibilities, please email former C/O robert.david.steele.vivas@gmail.com
Section V - Upcoming Events
AFIO EDUCATIONAL EVENTS IN COMING TWO MONTHS....
15
July 2015, 11:30am - 2pm - San Francisco, CA - The AFIO Andre LeGallo
Chapter hosts John Lightfoot, Assistant Special Agent in Charge of the
Counterterrorism branch in the FBI San Francisco Division.
Topic will be "Current Issues in Terrorism: Here and Over There".
ASAC Lightfoot will discuss Al-Q'aida today, the rise and threat of the
Islamic State, domestic groups and updates on recent Bay Area cases.
11:30AM no host cocktails; meeting starts at noon. Note different
location: Basque Cultural Center: 599 Railroad Ave, South San Francisco,
CA 94080.
E-mail RSVP to Mariko Kawaguchi at afiosf@aol.com with your meal choice (Salmon with Champagne Sauce OR Breast of Chicken
Chasseur) and you will be sent an Eventbrite link to register.
Alternately, mail a check made out to "AFIO" to: Mariko Kawaguchi, P.O.
Box 117578, Burlingame, CA 94011. Members and students: $25; non-members
$35. $35 at the door. RSVP is required by July 3, 2015 - no walk-ins.
Saturday, 8 August 2015, 11am - 3pm - Orange Park, FL - AFIO North Florida Chapter Meeting with John Caulfield, "Intelligence and the Department of State."
Our speaker that we disappointed in May, Mr. John Caulfield, is willing and eager to speak to us this time, and I am sure it'll prove most interesting -- not often we hear about the intelligence efforts of the Department of State. Mr. John P. Caulfield, retired American career diplomat who managed some of the most complex relations in Latin America for the United States, most recently as Chief of the U.S. Interests Section in Havana, Cuba. There he negotiated pragmatic agreements on immigration, environmental protection, civil aviation, and cultural affairs. He also supported the aspirations of ordinary Cubans for political rights and economic opportunities in a difficult environment.
Event location: Country Club of Orange Park.
Please RSVP to Quiel Begonia at qbegonia@comcast.net or call him ASAP at (904) 545-9549. Remember, spouses and interested friends or potential members are cordially invited. Cost for the luncheon is $24, pay the club.
Tuesday, 11
August 2015 - MacDill AFB, Florida - The AFIO Suncoast Chapter hosts
Karl D. Klicker, EdD, speaking on the Islamic State.
Dr. Karl Klicker is a retired Marine Corps
Intelligence Officer, currently employed by Jacobs Technology as
Principal Strategist supporting US Special Operations Command. He has
served on psychological operations, civil affairs, interagency task
force and strategic planning teams.
Klicker is the author of Indoc: Ideology, Propaganda and Conflict in the
Corps and al-Qaida, a study of internal cultural tensions within the
Marine Corps, the roots of division in the Sunni and Shi�a camps; the
social psychology of recruiting for war; and the ongoing conflict
between radical Islamists and America�s armed forces.
LOCATION: MacDill AFB Surf�s Edge Club, 7315 Bayshore Blvd, MacDill
AFB, FL 33621. Please RSVP by 15 August to the Chapter Secretary for yourself and include the names and email
addresses of any guests. Email or call Michael Shapiro at sectysuncoastafio@att.net. You will receive a confirmation via email. If
you do not, contact the Chapter Secretary to confirm your registration.
Check-in at noon; opening ceremonies, lunch and business meeting at 1230
hours, followed by our speaker.
FEE: You must present your $20 check payable to �Suncoast Chapter,
AFIO� (or cash) at check-in to cover the luncheon. If you make a
reservation, don�t cancel and get a cancellation confirmation by the
response deadline and then don�t show up, you will be responsible for
the cost of the luncheon.
25 - 26 August 2015 - McLean, VA - CIRA and AFIO's 40th Anniversary Conference and Celebration
CIRA (Central Intelligence Retirees Association) and
AFIO (Association of Former Intelligence Officers) are holding a joint conference and celebration of our 40th anniversaries
on 25-26 August 2015.
Day One - Tuesday, 25 August: This
celebration coincides with the next CIA Annuitant Reunion on 25 August
where many CIRA and AFIO members, who are CIA retirees, will be in
attendance.
AFIO and CIRA members who are CIA annuitants and who retired on an even year, have been invited directly by CIA and should sign up for
that day when the CIA invitation arrives in
your inbox. Annuitants of odd years who wish to attend may register
through the links below.
RESTRICTION: To attend Day One at CIA
you need to have been an employee, at some time, of any member agency of the Intelligence Community (or are now currently with,
or retired from, one of those agencies). A spouse accompanying you may
attend regardless of no prior IC employment. Restriction does not apply
to Day Two.
Day Two - Wednesday, 26 August: The
conference expands and continues on Day Two
at the Sheraton Tysons Hotel, with many CIA, CIRA, AFIO, and other IC
speakers and
panelists. This second day ends with a
"Spies in Black Ties"
Anniversary Reception and Awards Banquet.
 Invitation Letter to Members
Invitation Letter to Members
 Tentative Agenda
Tentative Agenda
To apply securely online, use form here.
To print-and-mail a  registration form, open it here.
registration form, open it here.
Space at this special event is limited.
If you have questions, contact afio@afio.com
Monday 28 September 2015 - New York, NY - AFIO Metro NY Chapter hears former FBI Special Agent Edward M. Stroz
Speaker Edward Stroz, former FBI, now with the
NYC-based firm of Stroz Friedberg, a global leader in investigations,
intelligence, and risk management. Topic and registration details to
follow in coming weeks.
Stronz was a Special Agent for the FBI before founding Stroz Friedberg
in 2000. He is an expert on electronic evidence and investigations,
internet extortions, denial of service attacks, computer hacking,
insider abuse, theft of trade secrets, electronic discovery matters, and
regularly provides expert testimony on these matters. Mr. Stroz
pioneered the use of behavioral science in investigations to gain
insights about intent and state-of-mind of computer users. He has
supervised hundreds of forensic assignments in assisting corporate
clients, trial counsel, individuals, and has conducted security
assessments for major public and private entities. While at the Bureau,
Stroz was responsible for the formation of the FBI�s Computer Crime
Squad in New York City, where he supervised investigations involving
computer intrusions, denial of service attacks, illegal Internet
wiretapping, fraud, and violations of intellectual property rights,
including trade secrets.
Location: Society of Illustrators building, 128 East 63rd St, between Park Ave and Lexington Ave.
COST: $50/person Cash or check, payable at the door only. Dinner to
follow talk & Q&A. Cash bar. RESERVATIONS: Strongly suggested,
not required, Email Jerry Goodwin afiometro@gmail.com or phone 646-717-3776.
16 November 2015, 12:30 pm - Los Angeles, CA - The AFIO - LA Chapter luncheon meeting with LA County Sheriff Jim McDonnell on Communications between Law Enforcement and Intelligence Agencies
Los Angeles County Sheriff Jim McDonnell will be the guest speaker for our November 2015 AFIO-L.A. Meeting. Sheriff McDonnell will be discussing the topic of improved communication between local law enforcement agencies and federal intelligence agencies, since September 11th and the role the Joint Terrorism Task Force (JTTF) played in improving mutual cooperation and shared gathered intelligence.
Bio of Sheriff Jim McDonnell
On December 1, 2014, Jim McDonnell took the oath of office and was sworn in as the 32nd Sheriff of Los Angeles County, the nation's largest sheriff's office and the seventh largest law enforcement agency in the United States, with 16,400 members and 400 reserve deputies.
Sheriff McDonnell served for 29 years at the Los Angeles Police Department, where he held every rank from Police Officer to second-in-command under Chief Bill Bratton. During his time at the LAPD, he earned that Department’s highest honor for bravery, the Medal of Valor, and led LAPD through the implementation of significant reforms. He helped create the blueprint for LAPD’s community-based policing efforts that have now become a model for law enforcement agencies throughout the nation.
For five years, Sheriff McDonnell served as the Chief of the Long Beach Police Department. In that role, he implemented numerous improvements that resulted in safer communities, increased morale, and enhanced community relations.
Sheriff McDonnell holds a Bachelor of Science degree in Criminal Justice from St. Anselm College in Manchester, New Hampshire and a Master’s Degree in Public Administration from the University of Southern California. He is also a graduate of the Federal Bureau of Investigation’s National Executive Institute and has completed executive education programs at Harvard’s Kennedy School of Government.
TO REGISTER: Lunch will be served for this event, please note the event is taking place on a Monday, more details to follow. Inquiries to AFIO_LA@yahoo.com.
Other Upcoming Events
Wednesday, 15 July 2015, noon - Washington, DC - The Billion Dollar Spy: Author Debriefing at the International Spy Museum
While getting into his car on the evening of February 16, 1978, the
chief of the CIA's Moscow station was handed an envelope by an unknown
Russian. Its contents stunned the Americans: details of top secret
Soviet research and development in military technology that was totally
unknown to the United States.
From David Hoffman, the Pulitzer Prize-winning author of The Dead Hand,
comes the riveting story of the CIA's most valuable spy in the Soviet
Union and an evocative portrait of the agency's Moscow station, an
outpost of daring espionage in the last years of the Cold War. Drawing
on previously secret documents obtained from the CIA, as well as
interviews with participants, Hoffman will reveal how the depredations
of the Soviet state motivated one man to master the craft of spying
against his own nation until he was betrayed to the KGB by a disgruntled
former CIA trainee. No one has ever told this story before in such
detail, and Hoffman's deep knowledge of spycraft, the Cold War, and
military technology makes him uniquely qualified to bring to the
International Spy Museum this real life espionage thriller.
Tickets: FREE! No reservation required. Visit www.spymuseum.org
14 October 2015, 6 - 9 pm - Arlington, VA - Silver Anniversary Gala and Chancellor's Dinner by Institute of World Politics
Since its founding, IWP has grown into the nation's premier graduate
school dedicated to developing leaders with a sound understanding of
international realities and the ethical conduct of statecraft, based on
knowledge and appreciation of the founding principles of the American
political economy and the Western moral tradition.
Location: The Ritz-Carlton, Pentagon City, 1250 South Hayes St, Arlington, VA 22202
Sponsorship & Tickets: For information on sponsorship opportunities
and ticket purchases, please contact Jennifer Giglio at 202.462.2101
ext. 312 or jgiglio@iwp.edu.
Accommodations:
A limited room block held at The Ritz-Carlton, Pentagon City is available at the rate of $269 per night.
To make your reservation, please click here. Input the Arrival Date, Departure Date and Group Code: WPGWPGA.
To make your reservation, by phone, please call 1.800.241.3333.
Reference the Group Name: The Institute of World Politics
Schedule of Events: 6:00 pm Cocktail Reception, 7:00 pm Dinner and Program
Keynote Speaker: Lt. Gen. Michael T. Flynn, USA (Ret.), 18th Director of the Defense Intelligence Agency
Entertainment: Keni Thomas, Award winning Nashville
singer-song writer and a decorated combat veteran with the elite 75th
Ranger Regiment special operations unit.
Attire: Black Tie or Military Dress Equivalent
Guests: An estimated 500 guests will gather to celebrate 25 years of The
Institute of World Politics' accomplishments and inspire the next
generation of leaders. The event will bring together national and
international civic and business leaders, members of Congress, and IWP
supporters to reflect on the work of the Institute.
Questions to Jennifer E. Giglio at JGiglio@iwp.edu.
Disclaimers and Removal Instructions
Weekly Intelligence Notes (WINs) are commentaries on Intelligence and related national security
matters, based on open media sources, selected, interpreted, edited and
produced for non-profit educational uses by members and WIN
subscribers.
REMOVAL INSTRUCTIONS:
We do not wish to add clutter to inboxes. To discontinue receiving the WINs:
a) IF YOU ARE A
MEMBER -- click here: UNSUBSCRIBE and supply your full name and email
address where you receive the WINs. Click SEND, you will be removed
from list. If this link doesn't open a blank email, create one on
your own and send to afio@afio.com with the words: REMOVE FROM
WINs as the subject, and provide your
full name and email address where you are currently receiving them.
b) IF YOU ARE NOT A MEMBER, and you received this message, someone forwarded this
newsletter to you [contrary to AFIO policies]. Forward to afio@afio.com the
entire WIN or message you received and we will remove the sender from
our membership and distribution lists. The problem will be solved for
both of us.
CONTENTS of this WIN
[HTML version recipients - Click title to jump to story or section,
Click Article Title to return to Contents. This feature does not work
for Plaintext Edition or for some AOL recipients]. If you wish to
change to HTML format, let us know at afio@afio.com. The HTML feature also does not work
for those who access their e-mail using web mail...however NON-HTML
recipients may view the latest edition each week in HTML at this link: https://www.afio.com/pages/currentwin.htm
WINs are protected by copyright laws
and intellectual property laws, and may not be reproduced or re-sent
without specific permission from the Producer. Opinions expressed in
the WINs are solely those of the editor's) or author's) listed with
each article. AFIO Members Support the AFIO Mission - sponsor new
members! CHECK THE AFIO WEBSITE at www.afio.com for back issues of the
WINs,
information about AFIO, conference agenda and registrations materials,
and membership applications and much more!
(c) 2000, 2012, 2013, 2014, 2015. Please note AFIO's new address: AFIO, 7600 Leesburg Pike, Suite 470 East, Falls Church, VA 22043-2004. Voice: (703)
790-0320; Fax: (703)
991-1278; Email: afio@afio.com
Click here to return to top.

![]() registration form, access it here.
registration form, access it here.  In the summer of 2011, the CIA Museum inaugurated a gallery dedicated to the Office of Strategic Services (OSS), the World War II outfit that was America’s first centralized intelligence agency. The Official OSS Exhibition Catalogue, like the gallery itself, brings the OSS legacy to life and suggests how the CIA reflects that legacy. Showcasing artifacts and photographs from the Museum collection, the catalogue covers the history of OSS from the Pearl Harbor attack through the dissolution of the OSS. Along the way, it introduces many trailblazers of US intelligence.
In the summer of 2011, the CIA Museum inaugurated a gallery dedicated to the Office of Strategic Services (OSS), the World War II outfit that was America’s first centralized intelligence agency. The Official OSS Exhibition Catalogue, like the gallery itself, brings the OSS legacy to life and suggests how the CIA reflects that legacy. Showcasing artifacts and photographs from the Museum collection, the catalogue covers the history of OSS from the Pearl Harbor attack through the dissolution of the OSS. Along the way, it introduces many trailblazers of US intelligence.
 All notices regarding the breach will come
from CSID, a private identity protection company hired by OPM to provide
services to those affected by the data breach. The notice you receive
may be either an email or a mailed letter. If an email, it will come
from opmcio@csid.com; a letter will
be on CSID letterhead and will contain phone numbers and websites to
contact them. Every individual whose personal information has been
compromised will be covered by a $1 million identity theft protection
policy and will have access to full-service identity restoration
provided by CSID. In addition, you will be offered the option to enroll
in the CSID Protector Plus program - free of charge for 18 months. Other firms, e.g., Life Lock, offer similar programs.
All notices regarding the breach will come
from CSID, a private identity protection company hired by OPM to provide
services to those affected by the data breach. The notice you receive
may be either an email or a mailed letter. If an email, it will come
from opmcio@csid.com; a letter will
be on CSID letterhead and will contain phone numbers and websites to
contact them. Every individual whose personal information has been
compromised will be covered by a $1 million identity theft protection
policy and will have access to full-service identity restoration
provided by CSID. In addition, you will be offered the option to enroll
in the CSID Protector Plus program - free of charge for 18 months. Other firms, e.g., Life Lock, offer similar programs. NEW: AFIO's Intelligence Community Mousepad
NEW: AFIO's Intelligence Community Mousepad
